Note:
To
make the entire site secure with HTTPS, configure the Secure
Web Page Settings page as shown below:
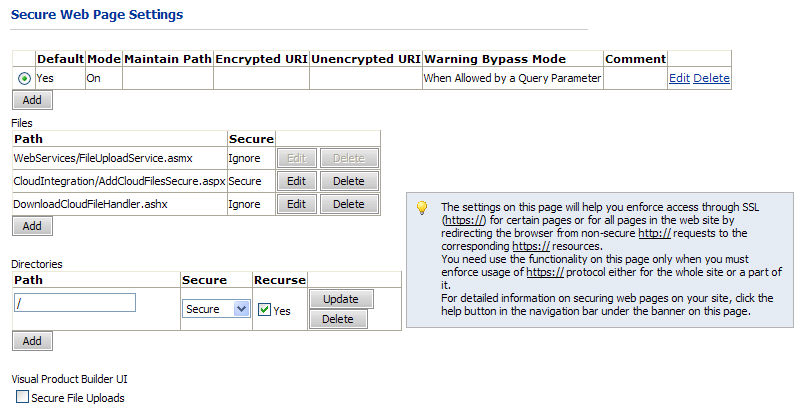
The settings on this page will help you enforce access through SSL (https://) for certain pages or for all pages in the web site by redirecting the browser from non-secure http:// requests to the corresponding https:// resources.
Note: For information on using visual verification (Captcha challenge-response) to protect your site against unauthorized use or security breaches, please see Configure User Self-Registration Settings.
You need use the functionality on this page only when you must enforce usage of https:// protocol either for the whole site or a part of it.
Note:
Nearly all web pages in your site will have a query string with data being
passed from page to page. Typically, this includes a brief name of the
exact page as well as various identifiers, such as file IDs or order IDs.
For instance, one may see this URL when previewing a file:
http://computername/[site
abbreviation]/Default.aspx?Content=PreviewFile&FileId=506
It is quite easy to copy one of these URLs, change the identifiers,
and then view data that is not your own. One way to make this much less
obvious is to encrypt the part that specifies the exact page and the identifiers,
known as the query string. This way, the URL looks something like this:
http://computername/[site
abbreviation]/Default.aspx?b4o5OcEi51ETk31gh9cbzz6jPI3QHkU5
If the encrypted part is modified, the string will not make sense
to the system and the home page will be shown instead. URL encryption
for your site is governed by settings on the Secure
Web Pages page. Complete these steps to activate URL encryption
for your site.
The page is divided into three sections—configurations, files, and directories:
● Configurations: allows the site administrator to maintain multiple HTTPS redirection schemes and designate the one the site is currently using.
Note: While all configurations are displayed on this page, only one is active at any one time (the one that has "Default" set to "Yes"). The main goal of having multiple configurations is to facilitate testing, either by the site administrator or technical support. A use case is that a site may be considering changes to their security settings. They can supply all of the settings in advance and only put the system into "test mode" briefly before reverting back. Another scenario is that technical support may be trying to troubleshoot an issue with the site and may want to temporarily turn off the use of HTTPS to rule this out as the cause of a problem. They may add a new configuration with HTTPS disabled, briefly switch to this, perform tests, and, after the problem is isolated and solved, switch imtely back to the customer's HTTPS configuration without losing any of the prior settings.
● Files: for the selected configuration specifies the redirection setting for individual resources (e.g. “login.aspx”, “*.asmx”, etc.).
● Directories: for the selected configuration specifies the redirection settings for the content of virtual directories (folders) on the web site (e.g. “/” – for the site root folder, “admin”, “WebServices”, etc.). These settings affect all the resources in the specified folder.
To manage secure web page settings
1. On the Secure Web Page Settings page, review the settings and make changes as needed.
Note: |
To
make the entire site secure with HTTPS, configure the Secure
Web Page Settings page as shown below: |
2. Set Configuration
Settings:
Each configuration has these settings:
● Radio Button: Indicates which configuration is selected (if more than one configuration is defined). Changing the selection revises the list of files and directories under the configuration grid.
● Default: Indicates which configuration is active—i.e., the one used by the web site.
Note: Upon changing the active configuration, it is advisable to imtely go to the Diagnostics page and clear the cache. This ensures that the new settings are applied imtely instead of after some delay.
● Mode: Specifies what requests are eligible to be mapped to HTTPS. Whether a particular request will actually be mapped to HTTPS depends on the file and directory information. The permitted values are:
● On: Permits mapping to HTTPS for all eligible requests, whether those requests are originating from the local server or from another location. Recommended for all sites using HTTPS, including those using credit cards.
● Remote Only: Permits mapping to HTTPS for only requests originating from outside of the server. No requests originating from the server itself are converted to HTTPS. Not recommended for any sites.
● Local Only: Permits mapping to HTTPS for only requests originating from this server. All other requests are left as HTTP. Not recommended for any sites.
● Off: Disables the use of HTTPS. .Appropriate for sites not using HTTPS. Also equivalent to using On but without files and directories.
● Maintain Path: Works in conjunction with Encrypted URI and Unencrypted URI properties. This flag indicates whether or not the module should maintain the current path when redirecting.
Note: In other words, if a user tries to access http://www.dsf50-site1.com/MyAccount/AccountInformation.aspx but the path is being maintained, switching to HTTPS mode for this page will take the user to http://www.dsf50-site1.com/MyAccount/AccountInformation.aspx. Without the path being maintained, the user will be taken to http://www.dsf50-site1.com. This must be set to Yes to ensure the proper operation of the web site. Note that No (unchecked) is the default value, conflicting with the value that we require for the web site to be functional.
● Encrypted URL / Unencrypted URL: Controls the URLs for the site, whether for HTTP or for HTTPS. In short, HTTPS requests will have the prefixed supplied in the Encrypted URL field, and HTTP requests will have the prefix supplied in the Unencrypted URL field. For example, you should have an encrypted URL of this format (https://www.dsf50-site1.com) and an unencrypted URL of this format (http://www.dsf50-site1.com)
Note:
There is no trailing site identifier like "/DSF" or "/ASP10"
or "storefront.aspx". Without these two values filled in, your
site will still work. Filling in these two values is only needed
if the domain or server names for the HTTP and the HTTPS site are different.
Consequently, we should strongly recommend that these simply be left empty.
The system does not validate directory and file names nor URLs in any way.
Typically, the Encrypted URL and Unencrypted URL fields should be left
blank. They are needed only if the server name or port number must be
overridden (for either HTTPs or HTTP redirect). If an invalid URL is entered
in these fields, your site will not open and function properly.
● Warning Bypass Mode: Controls the visibility of warnings when requests transition from HTTP to HTTPS as the user switches pages:
● Always Bypass : Always bypass security warnings when switching to an unencrypted page.
● When Allowed by a Query Parameter: Only bypass security warnings when switching to an unencrypted page if the proper query parameter is present. (Suggested and default.)
● Never Bypass: Never bypass security warnings when switching to an unencrypted page.
● Comment: Freeform text describing the nature of the configuration.
● Click Update.
3. Configure Files:
● Path: Contains a path from the web site root (such as Admin/OperatorView.aspx) to control security for that particular page.
Note: Wildcard names with a leading asterisk, such as “*.txt” can be used to specify a setting for all the files of the given type. However, if a setting is given for a specific file (e.g. “setupinstr.txt”), it overrides the wildcard-based setting for that file type. Files of these types: *.asmx (web service), *.axd (ASP.NET resource request handlers), and *.ashx (web request handlers) are always treated as Secure=Ignore even if not explicitly specified in the Files table.
● Secure: One of these settings as explained below:
● Insecure: Forces this page to be HTTP.
● Ignore: Does not force the page to be either HTTP or HTTPS. Instead, the same mode as the current request is used, without any forced transitions.
● Secure: Forces this page to be HTTPS.
● Click Update.
4. Configure Directories:
● Path: Contains a path from the web site root (such as /MyAccount or /Admin) so you can control security for that particular page.
Note: To secure all directories add the root directory by entering / in the Path field.
● Secure: One of these settings as explained below
● Insecure: Forces specified pages to be HTTP.
● Ignore: Does not force the specified pages to be either HTTP or HTTPS. Instead, the same mode as the current request is used, without any forced transitions.
● Secure: Forces specified pages to be HTTPS.
● Click Update.
To secure any page/s on your site, you must first enable HTTPS redirection:
1. Go to Administration > Secure Web Pages.
● If the topmost table has no entries, click Add below it.
● If the topmost table has one or more entries, select one row (using the radio button on the left), then click Edit on the right.
2. In the Default column, check Yes.
3. In the Mode column, select On from the pull-down list.
4. In the Maintain Path column, check Yes.
5. Encrypted URL / Unencrypted URL: Controls the URLs for the site, whether for HTTP or for HTTPS. In short, HTTPS requests will have the prefixed supplied in the Encrypted URI field, and HTTP requests will have the prefix supplied in the Unencrypted URI field. For example, you should have an encrypted URL of this format (https://www.dsf40-site1.com) and an unencrypted URL of this format (http://www.dsf40-site1.com).
Warning: The system does not validate directory and file names nor URLs in any way. Typically, the Encrypted URL and Unencrypted URL fields should be left blank. They are needed only if the server name or port number must be overridden (for either HTTPs or HTTP redirect). If an invalid URL is entered in these fields, your site will not open and function properly.
6. Select a Warning Bypass Mode: Controls the visibility of warnings when requests transition from HTTP to HTTPS as the user switches pages:
● Always Bypass : Always bypass security warnings when switching to an unencrypted page.
● When Allowed by a Query Parameter: Only bypass security warnings when switching to an unencrypted page if the proper query parameter is present. (Suggested and default.)
● Never Bypass: Never bypass security warnings when switching to an unencrypted page.
7. (Optional) Comment: Freeform text describing the nature of the configuration.
8. Click Update on the right.
To secure a single page:
1. In the Files section, click Add below the table to add a new row to the table.
2. In the Path column, type the relative path to a web page (e.g., Admin/ManageProducts.aspx), or a leading “*” wildcard (e.g. “*.asmx) in the “Path” column.
3. In the Secure column, select Secure from the pull-down list.
4. Click Update on the right.
To secure all admin pages:
1. In the Directories section, click Add below the table to add a new row to the table.
2. In the Path column, type “Admin”.
3. In the Secure column, select Secure from the pull-down list.
4. In the Recurse column, check the Yes checkbox.
5. Click Update on the right.